Introduction
Introduction
The article Computer Awareness Quiz 14 presents the important questions and answers to ace the Computer Awareness section in the competitive exams. Computer Awareness Quiz 14 covers many important questions for IBPS PO, SBI and RBI like exams and other similar tests.
The Computer Awareness questions related to History of computers, Introduction of computer, Basics of Hardware and software Input/Output Devices, Number System, Operating System basics, Basic Internet Knowledge and Protocol, Basic Functionalities of MS-Office, Networking and communication, Database Basics, Memory and storage device, Computer Shortcuts Key, Computer abbreviation, etc. The present article presents the questions related to the above-listed topics of Computer Awareness. In these days every recruiter feels that their employees should know the basics of the Computer Language. In most of the government recruitment exams, the computer awareness section (or) topic is present.
 Q1
Q1
A special, high-speed storage area within the CPU in which all data must be represented before it can be processed is called _____.
- A. BIOS
B. Cache
C. RAM
D. Register
Register is a special high-speed storage area within the CPU where all data must be represented before it can be processed.
Note:
For example, if two numbers are to be multiplied, both numbers must be in registers, and the result is also placed in a register.
 Q2
Q2
In terms of network what is meaning of SAP ?
- A. Smart Access Point
B. Service Access Point
C. Service At Point
D. Service Access Permission
A Service Access Point (SAP) is an identifying label for network endpoints used in Open Systems Interconnection (OSI) networking.
 Q3
Q3
The scrambling of code is known as_____.
- A. encryption
B. a firewall
C. scrambling
D. password-proofing
The scrambling of code is known as encryption. It is the process of converting information or data into a code, especially to prevent unauthorized access.
 Q4
Q4
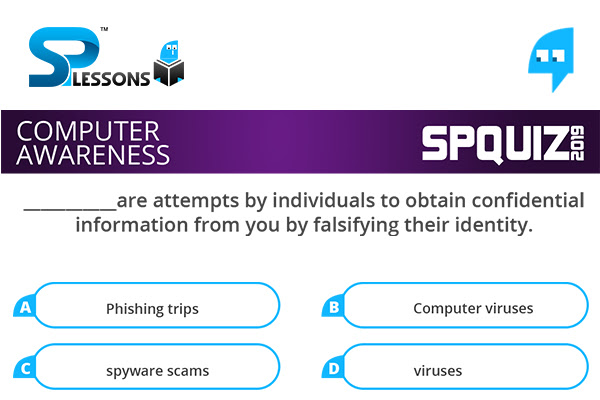
___________are attempts by individuals to obtain confidential information from you by falsifying their identity.
- A. Phishing trips
B. Computer viruses
C. spyware scams
D. viruses
Phishing trips are attempts by individuals to obtain confidential information from you by falsifying their identity.
 Q5
Q5
A special type gateway that can keep external users from accessing resources on the LAN users access the external info is called ______.
- A. Repeater
B. Firewall
C. Encryption
D. Hub
A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network.